7 Best Meme Coin Trading Tools for 2026
Discover the 7 best meme coins trading platforms and tools for 2026. Get actionable insights, find winning wallets, and trade smarter on CEXs and DEXs.

February 20, 2026
Wallet Finder

February 18, 2026

Before you invest in a new token or DeFi project, learning how to perform a rug check is your most critical skill. It’s the process of investigating a project for red flags that suggest developers plan to vanish with investor funds. This guide provides an actionable checklist for every crypto trader, especially those navigating the high-risk memecoin market.
Decentralized Finance (DeFi) and memecoins offer the potential for massive returns, but this high-reward environment is filled with the constant threat of rug pulls. These scams are rampant in crypto's less-regulated corners, where hype and anonymity can easily mask malicious intent. Losing everything to a project that seemed promising is a painful, yet common, story.
According to Chainalysis, rug pulls drained $2.8 billion from investors in 2021 alone, accounting for nearly a third of all crypto theft that year. The threat is real and significant.
A rug check is a systematic method of vetting a project before you risk your capital. By learning what to look for, you shift from being a potential victim to an informed investor. This guide provides the tools to spot the most critical warning signs early by covering three key areas:
A thorough rug check is what separates strategic investing from pure gambling. It empowers you to make decisions based on data, not just hype or FOMO (fear of missing out).
Mastering this process is about protecting your portfolio. You'll learn how to identify potential liquidity issues, which are often a precursor to extreme volatility and scams. For a deeper look at this topic, read our guide on why low liquidity increases meme token volatility.
This guide provides a repeatable process to evaluate any new crypto project. Here is a quick reference table to get you started.
This table maps out the critical checkpoints. As we go through each one in detail, you'll learn exactly what to look for and which tools can help you find the answers you need.
The blockchain is an immutable public ledger, providing a source of verifiable data. A real rug check starts here—by moving past social media hype and digging into the hard facts recorded on-chain.
This visual decision tree offers a straightforward flow for assessing risk, from a token's potential to non-negotiable safety checks like liquidity and team transparency.
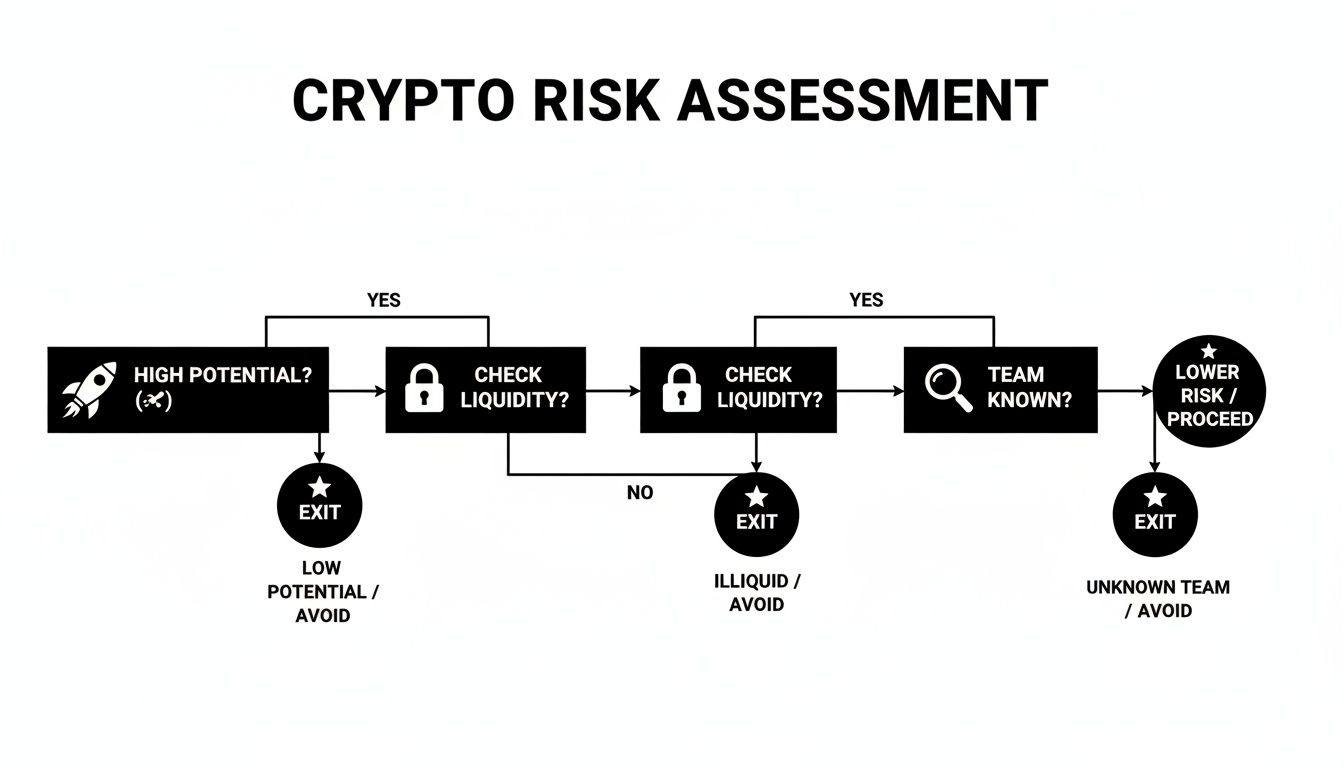
A solid investment must pass multiple checkpoints. High potential is worthless if the project's fundamentals are flawed.
The smart contract is the project's digital DNA, containing rules that can be designed to trap investors. You don't need to be a coding expert to spot the most common dangers.
Actionable Steps:
Key Red Flags to Look For:
When a project launches, developers pair their token with a major crypto (like ETH or SOL) in a liquidity pool (LP). A classic rug pull occurs when they withdraw this liquidity, making the token unsellable. Trustworthy teams "lock" or "burn" their LP tokens to prevent this.
Actionable Steps:
0x000...00dEaD).A project with less than 90% of its initial liquidity locked for at least six months is an immediate red flag. Don't be fooled by short-term locks or a low percentage—they offer zero real security.
A project where a few wallets control most of the tokens is a ticking time bomb. Those top holders can crash the price instantly by dumping their tokens.
Actionable Steps:
Key Red Flags to Look For:
This type of on-chain analysis reveals who truly holds power. For more detail, read our guide on the fundamentals of on-chain analysis.
A honeypot is a scam contract that allows you to buy tokens but prevents you from selling them.
Actionable Steps:
A secure smart contract is meaningless if the team behind it is anonymous or dishonest. Off-chain analysis—investigating the human element—is a non-negotiable part of any serious crypto rug check.
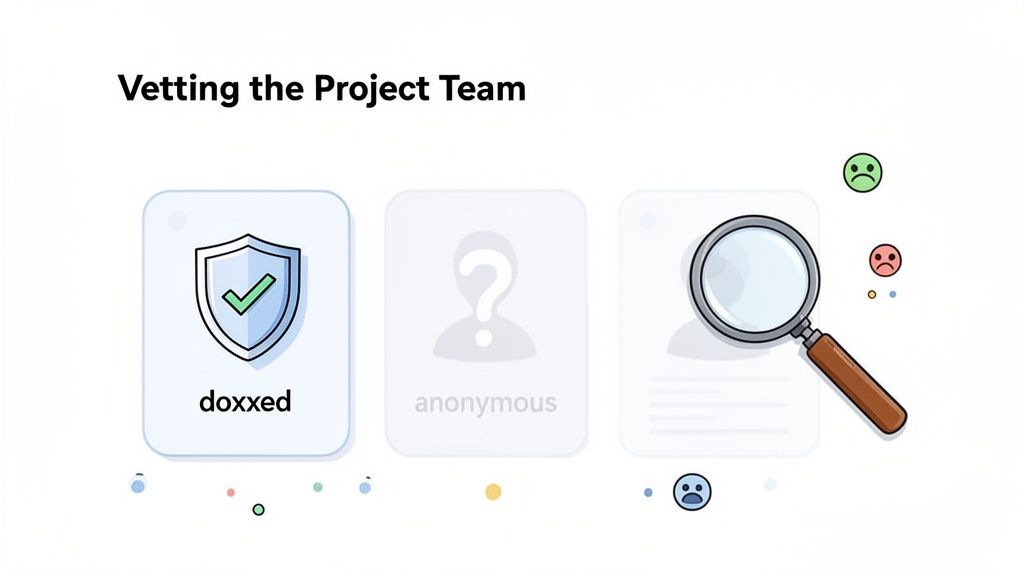
This is especially critical in the memecoin space, where an estimated 80% of all DeFi rug pulls occur. Scammers weaponize hype and anonymity to execute their schemes.
A doxxed team has publicly revealed their real-world identities. This is a massive green flag, as it creates accountability. Developers with their names and reputations on the line are far less likely to commit fraud. An anonymous team is an immediate red flag. While a few legitimate projects have anonymous founders, they are the exception.
A transparent team with a verifiable public history is one of the strongest signs of a project's legitimacy. If the founders are ghosts online, proceed with extreme caution.
A project's whitepaper and roadmap outline its vision. However, many are just marketing documents filled with buzzwords and empty promises.
Actionable Checklist for Reviewing Documents:
For a deeper dive, our guide on how to properly analyze a crypto white paper can help you distinguish a solid plan from pure hype.
A project's community on platforms like Telegram, Discord, and X (formerly Twitter) is revealing. Learn to separate genuine engagement from a facade built with bots and paid shills.
Social Media Red Flags Checklist:
A healthy community balances excitement with critical discussion. If all you see is relentless, one-sided hype, something is wrong.
Manual checks are essential, but the crypto market moves too fast for them to be your only defense. To protect your capital effectively, you need a system for continuous, automated monitoring. This is how you spot trouble before it starts.
Advanced tools provide real-time alerts on specific wallet activities, offering a significant advantage in risk management.
One of the most powerful strategies is to monitor the wallets of project insiders. When developers or early investors move large amounts of tokens to an exchange, it often precedes a major price dump.
You can use a platform like Wallet Finder.ai to create a custom watchlist of these key wallets and set up instant notifications for suspicious activity.
Proactive monitoring allows you to act on the on-chain data that causes price movements, rather than reacting to the aftermath.
Beyond tracking individuals, you can set up alerts for specific on-chain events that signal danger. These automated monitors work 24/7, catching activity that manual checks would miss.
A sudden, large removal of liquidity from a project's main trading pool is one of the most classic, blatant signs of a rug pull. An alert for this one event can be the difference between a small loss and getting completely wiped out.
Consider setting up alerts for these critical events:
Monitor the activity of "smart money" wallets—those belonging to seasoned, successful traders. If you see these respected players buying into a new project, it can be a strong vote of confidence. Conversely, if they are avoiding a hyped token, their silence is telling.
Tools that analyze the performance of top wallets can help you identify these key players. Watching their moves allows you to piggyback on their research, adding a crucial layer of social proof to your rug check process.
Theory is useful, but analyzing real-world scams makes the lessons stick. By dissecting infamous rug pulls, we can see how the red flags we've discussed appear in actual scenarios.
These case studies are practical examples of how a solid rug check crypto process could have prevented massive losses. Each disaster left a clear trail of on-chain evidence visible long before the collapse.
The SQUID token combined social hype with a malicious smart contract. It launched on the fame of the hit Netflix show, and investors piled in as the price went vertical. The problem? No one could sell.
This was a classic honeypot scam. The contract contained a function that blocked anyone but whitelisted wallets from selling the token.
A few basic on-chain checks would have exposed this immediately:
The SQUID token rug pull is a perfect example of why the simple "can I sell this?" test is your most important first step.
Another textbook rug pull involves a project with a centralized token supply. A new memecoin launches, its price skyrockets, and then plummets 99% hours later. The cause? A small group of connected "whale" wallets.
In this scenario, a tool like Bubblemaps would have revealed the truth. The top five wallets, all funded from the same source address, controlled over 40% of the supply. These insiders waited for retail to build up liquidity, then dumped their tokens, draining the pool and leaving everyone else with worthless assets.
By analyzing holder distribution before you even think about buying, you can spot these rigged games from a mile away. A project with a truly decentralized holder base is always a healthier, more resilient bet.
Many scams appear on networks with low transaction fees like BNB Smart Chain (BSC), as it's cheap for scammers to operate. In fact, BSC hosted roughly 71% of all rug pull scams in 2024. You can explore more cryptocurrency scam statistics to understand the broader landscape.
By following the checklists in this guide, investors could have easily spotted these red flags and avoided becoming exit liquidity.
Here are answers to some of the most common questions traders have when vetting new crypto projects.
Absolutely not. A smart contract audit is a critical step but is not a foolproof guarantee against a rug pull. Auditors check code for technical vulnerabilities, not the team's intentions. A project with a perfect audit can still be a scam if the founders control the liquidity or hold a majority of the token supply. An audit is just one checkpoint among many.
Yes. The core principles of a rug check are universal, though the specific tools may differ by blockchain. Whether you're on Ethereum, Solana, Base, or another network, you are looking for the same fundamental red flags.
The questions remain the same, only the platform for finding answers changes.
If a project's liquidity is not locked or burned, walk away. Don't even think twice. It's the most glaring and dangerous red flag you can find.
Unlocked liquidity gives developers a direct and easy way to drain the entire pool and disappear with investor funds. While an anonymous team or a dead social media presence are concerning, unlocked liquidity is the technical vulnerability that enables the classic rug pull. There is virtually no legitimate reason for a new project to keep its primary liquidity pool unlocked.
The best defense against getting rugged is a proactive offense. Instead of just reacting to price dumps, you need to see them coming with real-time on-chain data. Wallet Finder.ai equips you with the tools to monitor insider wallets, track smart money moves, and get instant alerts on sketchy activity. It turns confusing data into clear, actionable intelligence. Start your free trial at https://www.walletfinder.ai and trade with an unfair advantage.