7 Best Meme Coin Trading Tools for 2026
Discover the 7 best meme coins trading platforms and tools for 2026. Get actionable insights, find winning wallets, and trade smarter on CEXs and DEXs.

February 20, 2026
Wallet Finder

February 17, 2026

Ever heard the term 'rug pull' in crypto circles? It's one of the most common—and devastating—scams. A rug pull is a nasty exit scam where a crypto project's developers abandon it, taking investors' money with them.
Imagine investing in a groundbreaking startup. The team is charismatic, marketing is slick, and hype is through the roof. Then, you wake up to find their website gone, social media deleted, and the founders have vanished with every dollar. That’s a crypto rug pull. Your once-promising tokens are now worthless, their value plummeting to zero almost overnight.
A rug pull gets its name from "pulling the rug out from under someone." It’s a perfect metaphor for how investors feel when developers they trusted suddenly disappear, leaving them with nothing. These scammers build fake credibility with aggressive marketing to get people to buy their new token.
Once they've collected enough cash, they pull the plug. They might drain money from the liquidity pool, dump their massive stash of tokens on the market, or steal funds locked in smart contracts. The outcome is always the same: a catastrophic price crash, often wiping out over 90% of the token's value in hours. For more detail, there are great technical breakdowns of cryptocurrency rug pulls available.
A rug pull is fundamentally an act of betrayal. Developers build a community, promise innovation, and then exploit that trust for personal gain, leaving a trail of financial destruction.
Learning to spot the signs of a rug pull is your first line of defense. While methods can differ, most scams share common traits. These red flags are often hiding in plain sight, disguised by hype and FOMO.
Here's a breakdown of defining features you'll typically find in a rug pull scheme.
CharacteristicDescriptionImpact on InvestorsAnonymous CreatorsThe development team hides their real-world identities behind pseudonyms or fake profiles.Makes it nearly impossible to hold anyone accountable or seek legal recourse after the funds are stolen.Sudden Liquidity RemovalDevelopers withdraw all the funds from the decentralized exchange's liquidity pool.Instantly makes the token untradeable, trapping investors' funds and crashing the price to zero.Disabled Selling FunctionsThe token’s smart contract is coded to allow buying but prevents or restricts selling by regular users.Creates a one-way market where the price is artificially inflated until the developers cash out.
Recognizing these characteristics early can be the difference between avoiding a scam and becoming another statistic.
Not all rug pulls follow the same script. Scammers use a few distinct methods to pull the rug out. Understanding how these scams work is the first step toward spotting them.
The typical process moves from manufactured excitement straight to an abrupt exit.
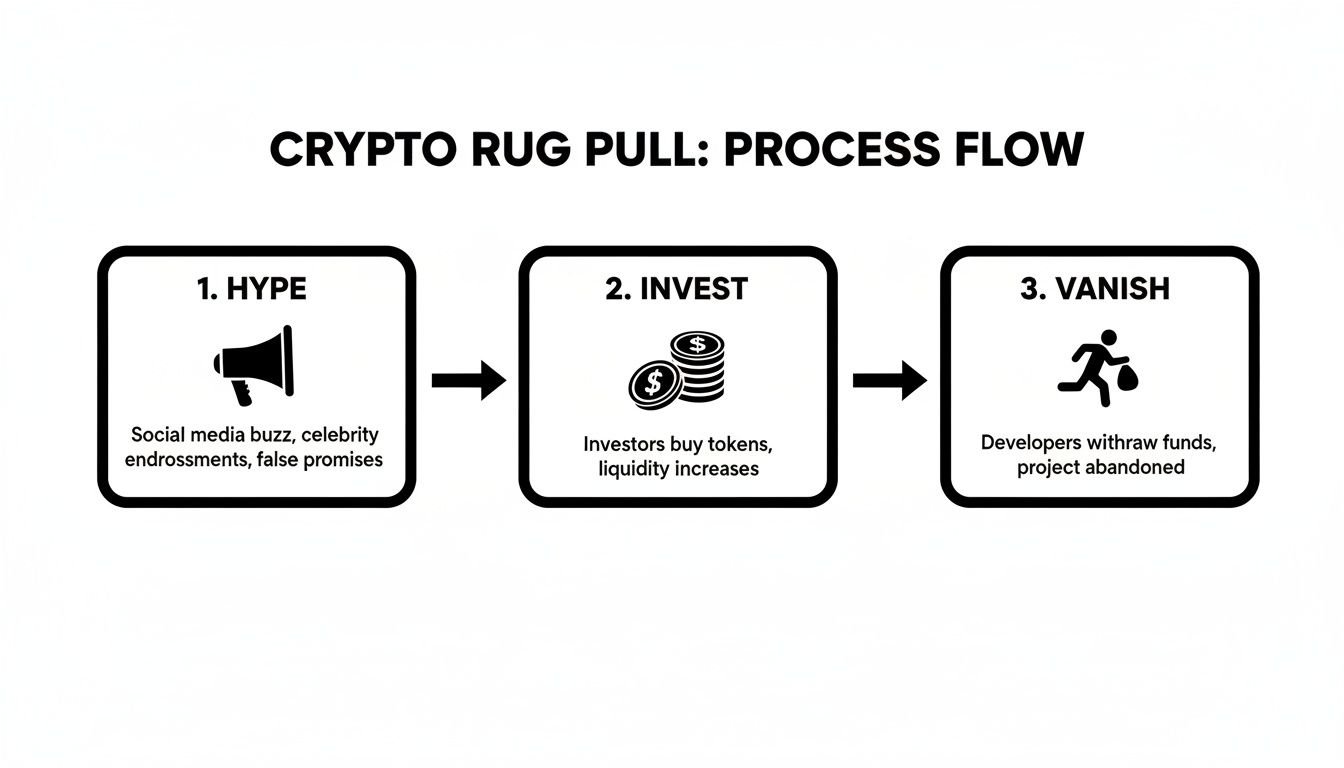
This three-step cycle shows how scammers play on community hype to attract capital before disappearing. Let’s break down the three main types of rug pulls.
The most common and technical type is the liquidity pull. To make a new token tradable on a decentralized exchange (DEX), developers create a liquidity pool. They pair their new token with an established crypto like Ethereum (ETH) and lock them in a smart contract.
This pool allows users to swap ETH for the new token. Scammers wait until a ton of investor ETH has flooded into the pool. Then, they suddenly withdraw all the liquidity, snatching the valuable ETH and leaving behind worthless project tokens.
A liquidity pull is like a currency exchange owner running off with all the U.S. dollars, leaving customers holding a currency that can no longer be traded. It makes selling impossible and instantly drains the token's value.
A simpler but equally devastating method is the token dump, or "sell-off." Here, developers hold a massive percentage of the total token supply from the start. They generate hype and wait for the price to climb as investors buy in.
Once the price peaks, the developers "dump" their entire stash on the market in one massive sell-off. This flood of supply instantly crashes the token's price, often by 99% or more. Other investors are left with worthless assets while the founders walk away with millions.
Perhaps the most devious type is the honeypot scam. Here, malicious code is baked into the token's smart contract. The contract is written to allow users to buy the token but stops them from ever selling it.
Investors purchase the token, watch its price go up, and think their investment is doing great. But when they try to cash out, the transaction fails. Only the developers' wallet address is whitelisted to sell. For a deeper look, it's worth exploring smart contract security.
The existing section on honeypot scams correctly identifies that malicious code is baked into the token contract. What it doesn't explain is how an ordinary investor with zero coding background can read that code before investing, because the smart contract for every token on Ethereum, BNB Chain, and most other major blockchains is publicly visible and partially interpretable without any technical knowledge. The tools that do the heavy lifting already exist and are free. Most investors simply don't know to use them.
Every token deployed on Ethereum has a contract address, a unique identifier that starts with "0x." Paste that address into Etherscan.io and navigate to the Contract tab. If the contract is verified, you can read the actual source code. If it is unverified, that is itself a major red flag. Legitimate projects almost always verify their contracts because verification is free, fast, and signals transparency. An unverified contract is one the team does not want you to read.
In a verified contract, you are not looking to understand all the code. You are scanning for specific function names and patterns that signal danger. The most important ones to search for (use Ctrl+F in your browser on the contract source page):
"blacklist," "blocklist," or "ban" appearing in transfer-related functions indicates the contract owner can prevent specific wallet addresses from selling. This is the primary mechanism used in advanced honeypot scams where not all buyers are blocked from selling, only those the team decides to blacklist after they have bought in.
"mint" appearing outside the initial token creation context, particularly in a function that is callable by the contract owner at any time, means the team can create new tokens indefinitely and dilute your holdings or crash the price by minting and dumping at will. Legitimate tokenomics set a fixed supply at launch and remove minting ability afterward.
"setFee," "setTaxBuy," or "setTaxSell" with no upper limit capped in the code means the team can change the transaction tax to 99% after you buy, effectively preventing profitable selling without technically blocking it. This is one of the most common patterns in sophisticated honeypots on BNB Chain.
"owner" functions that are not renounced mean the deployer retains admin control over the contract. Check the "Read Contract" section on Etherscan for a function called "owner." If it returns a live wallet address rather than the zero address (0x0000...0000), the team still controls the contract. Legitimate projects frequently "renounce ownership" after launch, which removes their ability to make changes. Ownership renouncement is not foolproof (some backdoors survive it), but unrenounced ownership on a project claiming to be decentralized is contradictory.
For investors who want faster analysis without reading code manually, three free automated tools decode contract risk in seconds.
Token Sniffer (tokensniffer.com) runs automated security checks on any token contract address and returns a risk score with specific findings, flagging honeypot functions, copycat code, and ownership issues in a single dashboard. It covers Ethereum, BNB Chain, and several other networks.
Honeypot.is specifically tests whether a token is a honeypot by simulating a buy and sell transaction and reporting whether the sell succeeds and at what effective tax rate. It is the fastest single check for the most common attack type and takes about 10 seconds per token.
De.Fi Shield (formerly DeFi Safety) provides a comprehensive contract audit score alongside team and tokenomics analysis, aggregating multiple risk signals into a single rating. It covers more chains than Token Sniffer and includes historical scam pattern matching.
None of these tools catch every scam. A sufficiently sophisticated team can write code that passes automated scanners while retaining hidden control mechanisms. But they eliminate the most obvious and most common attack patterns before you invest a dollar, which reduces your exposure to the vast majority of rug pulls that use standard templates.
Figuring out if a project is a potential rug pull takes detective work. Scammers almost always leave clues in how they present their project and in the blockchain data itself. Learning to spot these is the single most important skill to protect your crypto.
Think of it like buying a used car. You’d check for dents and listen for a weird engine noise (off-chain), but you’d also want the vehicle history report to check for accidents (on-chain data). You need both to avoid buying a lemon.
Warning signs can be split into two camps: signals in the project's community and communications (off-chain) and hard evidence from the blockchain (on-chain).
Indicator TypeOn-Chain Example (Data-Driven)Off-Chain Example (Qualitative)Team & OwnershipConcentrated Token Ownership: A few wallets hold a massive % of the supply.Anonymous or Hidden Team: No real names, faces, or professional histories.Security & CodeNo Smart Contract Audit: The code has not been checked by a reputable firm.No Technical Whitepaper: The project's goals are vague, full of buzzwords, or copied.LiquidityUnlocked Liquidity Pool: Devs can withdraw all the funds at any time.Constant Hype About Price: The focus is on "getting rich quick," not technology.CommunitySuspicious Transaction Patterns: Lots of small, repetitive buys from new wallets.Bot-Filled Social Media: Fake engagement, no real discussion or critical questions.
While off-chain signs are great for a gut check, on-chain data is where you find undeniable proof.
Off-chain red flags are the qualitative signals from how a project presents itself. They are often the fastest and easiest things to check. Here is an actionable checklist:
This is where you move past what the team says and verify things with data from the blockchain. On-chain analysis uncovers the risks they'd rather you not see. Use automated tools and crypto scam checkers to do the heavy lifting.
The blockchain doesn't lie. Scammers are great at making slick websites and faking social media engagement, but they can't hide shady on-chain activity like unlocked liquidity or giving all the tokens to their friends.
Here are the big on-chain indicators you can't afford to ignore:
To understand what a rug pull is, you have to look at the money involved. These aren't small-time annoyances. They're a multi-billion dollar problem that has wiped out investors worldwide, especially as decentralized finance (DeFi) has taken off.
The boom in DeFi protocols accidentally rolled out the red carpet for scammers. Creating and listing new tokens on decentralized exchanges became incredibly easy, which meant fraudulent developers could launch projects with almost zero accountability.
The sheer scale of these scams tells you everything: the easier it is to create a project, the more work you, the investor, have to do. Scammers love environments where hype drowns out fundamentals.
The financial damage from rug pulls is staggering. The year 2021 was a turning point—rug pulls made up 37% of all crypto scam revenue. That’s around $2.8 billion snatched from investors, a massive jump from just 1% in 2020.
This spike went hand-in-hand with the DeFi boom, where rug pulls became the scam of choice. Countless new tokens were minted for the sole purpose of draining investors' money. For a deeper dive into the numbers, check out the full crypto crime report from Chainalysis.
Knowing how much money is on the line makes it clear why due diligence is so critical.
Scammers are incredibly good at adapting. They pivot their tactics to whatever is new and hot, targeting whatever trend has investor FOMO (Fear Of Missing Out) at a fever pitch.
Here’s a quick look at how rug pulls have changed with the times:
The hype phase of a rug pull is not organic. The social media excitement, the surging trading volume, the sense that everyone is piling in simultaneously — these are manufactured, and understanding the specific mechanics behind them turns what looks like genuine momentum into a readable set of warning signals on your blockchain analytics tools.
Wash trading is the practice of buying and selling the same asset between wallets you control to generate artificial transaction volume. In a rug pull context, the development team deploys multiple wallets, often dozens or hundreds, and cycles funds between them to create the appearance of active trading. On DEX aggregators like DexScreener and GeckoTerminal, this shows up as high trading volume relative to the pool's liquidity, which is the first specific metric to check.
A legitimate token with $500,000 in liquidity typically sees daily trading volume of 20% to 100% of that liquidity pool size, meaning $100,000 to $500,000 in daily volume. This ratio reflects genuine demand relative to available supply. A rug pull token with $500,000 in liquidity showing $3 million to $10 million in daily volume is almost certainly wash trading. Volume that is 5x to 20x the liquidity pool size cannot be explained by organic demand because organic traders would exhaust the pool's liquidity at those ratios. The volume is circular, cycling between the team's own wallets.
On DexScreener, pull up any token and look at the "Txns" column, which shows the number of buy and sell transactions. In wash trading patterns, you see either a near-perfect 1:1 buy-to-sell ratio (both sides of the circular trade appearing as separate transactions) or wildly imbalanced ratios (many more buys than sells) when the team is front-loading buy pressure to drive price up before their dump. Organic tokens show messier, more varied buy-sell ratios because they reflect the uncoordinated decisions of many independent traders.
The individual wallets executing wash trades share a specific characteristic that makes them identifiable on Etherscan and similar block explorers: they are brand new. A wallet created 12 hours before the token launch that has only ever interacted with this specific token and no others is almost certainly a bot wallet controlled by the development team. The wallet age check takes 30 seconds on any block explorer.
Look at the top 10 to 20 token holder wallets under the "Holders" tab on Etherscan. Click each wallet address and check when it was first active (the date of its first transaction). If the majority of large holders have wallet creation dates within days of the token launch, with no prior transaction history on other tokens, you are looking at a team-controlled wallet cluster. Legitimate retail investors who buy early typically have wallets with months or years of prior activity across multiple tokens and protocols.
One final manufactured signal worth understanding is the liquidity-to-market-cap ratio that rug pull teams deliberately set to attract attention from token discovery platforms. CoinGecko and CoinMarketCap both surface newly listed tokens, and tokens with very low liquidity relative to their market cap appear to have enormous potential upside based on surface metrics.
A token with 1 billion total supply, a price of $0.001, and a market cap of $1 million with only $50,000 in liquidity looks like a tiny project with massive room to grow. In practice, a $50,000 liquidity pool on a $1 million market cap token means any significant sell pressure instantly craters the price because there is not enough liquidity to absorb it. The team needs minimal capital to maintain the illusion of value while they accumulate their dump position. The moment they sell even $30,000 worth of tokens into a $50,000 pool, the price collapses by 60% or more. Always check liquidity pool size directly, not just market cap.
Knowledge is your best defense, and on-chain analysis tools are your secret weapon. While red flags in whitepapers and shady social media are helpful, the blockchain holds the undeniable truth. Platforms like Wallet Finder.ai are built to turn this raw data into actionable intelligence.
Instead of just reacting after a scam, you can get ahead by vetting projects before you invest. It’s like having a private investigator for the blockchain. You can dig into the digital footprints of creators, track developer wallets, and spot suspicious activity long before the rug gets pulled.
On-chain tools pull back the curtain on complex blockchain transactions. They let you see who holds the most tokens, when team wallets are moving huge sums, and how experienced traders are positioning themselves.
Here’s an actionable list of checks you can perform with these tools:
On-chain analysis is the ultimate lie detector. A team can promise you the world, but their wallet activity reveals their true intentions. Large, unexplained token movements don't lie.
Let's make this concrete. Imagine you're sizing up a new DeFi token. Instead of just taking their website at face value, fire up a tool like Wallet Finder.ai. In seconds, you can visualize who holds what and how the money is flowing, answering the critical questions that protect your capital.
This is what it looks like inside a platform like Wallet Finder.ai, which makes it easy to track wallets.

The interface translates complex blockchain events into a clear dashboard, highlighting key metrics like PnL and trade history for specific wallets. This lets you identify traders who consistently sidestep rug pulls and make profitable moves, giving you a blueprint for safer strategies.
Ultimately, these tools empower you to shift from passive speculation to data-driven investing.
The article correctly notes that recovering funds after a rug pull is extremely difficult. The more complete picture explains exactly why, because the reasons are specific and instructive for anyone considering filing a report or exploring legal options. There have been successful prosecutions and fund recoveries, and understanding what made those cases work reveals the specific conditions required for legal action to produce any outcome.
The fundamental problem with rug pull prosecution is not a lack of evidence. Blockchain transactions are permanently recorded and publicly visible, making them among the most traceable financial crimes in history. The problem is jurisdictional fragmentation and identity mapping. Prosecutors can see every transaction, but they need to connect those blockchain addresses to real-world identities before they can charge anyone. When developers operate under pseudonyms, use privacy wallets like Tornado Cash or Railgun to obscure the movement of stolen funds, and operate from jurisdictions with no crypto regulatory framework or no extradition treaty with the US, the evidentiary chain breaks before a case can be built.
The US Department of Justice has successfully prosecuted several rug pull cases where developers made identifiable mistakes. The Frosties NFT rug pull in 2022 resulted in the arrest and eventual conviction of Ethan Nguyen and Andre Llacuna. The key error they made was linking their NFT sales proceeds to exchanges that had their KYC (Know Your Customer) information on file. The blockchain showed the funds moving from the Frosties contract to a specific wallet, then to a centralized exchange. The exchange's compliance team provided the KYC records to investigators under a subpoena, and those records connected the wallet to a real person with a real address. The entire forensic chain took less than two months to reconstruct.
South Korea has been more aggressive than most jurisdictions in prosecuting crypto fraud. The Luna/Terra collapse investigation resulted in the arrest of Do Kwon in Montenegro in 2023 and his subsequent extradition to South Korea. South Korean financial regulators combined blockchain analytics with traditional financial surveillance and international arrest warrants to pursue a case that involved billions of dollars. The scale justified the resources.
If you have been victimized by a rug pull and want to preserve evidence for a potential report to the FBI's Internet Crime Complaint Center (IC3) or to your country's equivalent financial crime authority, the specific data worth preserving includes: the contract address of the token, your transaction hashes showing purchase and failed sale attempts, the deployer wallet address, the liquidity withdrawal transaction hash (this is the specific transaction where the team drained the pool, and it is permanently on chain), and screenshots of all off-chain communications including Telegram announcements, Discord messages, and Twitter posts from the project's accounts before they were deleted.
Law enforcement agencies with crypto forensics capability use tools like Chainalysis Reactor and Elliptic Navigator to trace fund flows across chains and through mixing services. These tools are not available to retail investors, but the underlying blockchain data they analyze is. Preserving the raw transaction data listed above gives investigators a starting point they can build on without having to reconstruct your personal research from scratch.
The honest assessment remains that for rug pulls under approximately $1 million and involving developers in jurisdictions outside the US, EU, South Korea, or Singapore, the practical probability of recovery through legal channels is very low. This is not a reason to avoid reporting, because aggregate complaint data helps regulatory agencies identify patterns and prioritize enforcement resources, but it is a reason to treat prevention as the only reliable protection.
Just spotting red flags isn't enough. You need a disciplined, proactive approach to investing. Think of it as a framework that naturally weeds out sketchy projects.
The cornerstone is simple: portfolio diversification. Don't put all your eggs in one basket. By spreading your capital across different assets, you ensure a single scam won't zero out your portfolio.
Next is your research process. You have to dig deep and think for yourself, because relying on social media hype is a fast track to getting wrecked. Prioritize projects with transparent, publicly doxxed teams. And most importantly, insist on seeing a third-party smart contract audit.
Finally, get a handle on the psychological side of trading. Master your emotions and resist FOMO (Fear Of Missing Out). Scammers are experts at creating a sense of urgency to pressure you into jumping in without thinking.
The most profitable move is often the one you don't make. Patience and diligence are your greatest assets in a market designed to trigger impulsive decisions.
History shows scams surge when the market gets hot. The NFT boom of 2021-2022 unleashed a tidal wave of rug pulls. Platforms like Pump.fun have seen a staggering 98.6% of new tokens in 2024 flagged as scams. These trends make it clear why a disciplined framework is essential. You can dig deeper into crypto rug pull trends over on Coincub.
A huge part of this is learning to recognize different tricks scammers pull. To get up to speed, check out our guide on common DeFi wallet scams. By making these habits second nature, you build a robust defense that protects your capital.
We get it. It’s a lot to take in. Here are answers to common questions about rug pulls.
To be blunt: probably not. Recovering funds after a rug pull is incredibly difficult, bordering on impossible.
Because crypto transactions are decentralized and often anonymous, once scammers have your money, there’s usually no way to get it back. This harsh reality is why prevention and doing your homework upfront are everything.
Absolutely not. Innovation drives crypto forward, and many new projects are legitimate.
However, the risk is always higher with brand-new, unaudited projects—especially if the team is anonymous and their marketing feels too aggressive. You have to treat every new investment with a healthy dose of skepticism and run it through the red flag checklist.
A smart contract audit from a reputable firm is a huge green flag, but it's not a silver bullet. An audit checks the code for bugs and security holes; it can't verify the team's true intentions.
Think about it: a project can have a perfectly secure contract, but if the founders hold a massive chunk of the token supply, there’s nothing stopping them from dumping it on the market. That's why you always need to pair audit checks with your own on-chain analysis.
Yes, and this is one of the most dangerous misconceptions in crypto security. An audit is a code review performed at a specific point in time by a third-party firm. It identifies bugs, vulnerabilities, and code that does not match the project's stated intent. What an audit cannot verify is developer intent, and intent is what makes a rug pull a rug pull rather than a technical failure.
The most common audit-related deception involves the timing of contract modifications. A team commissions an audit of one version of their contract, receives a clean bill of health, publishes the audit report, and then deploys a different version of the contract that adds malicious functions. Investors see the audit report, assume it covers the deployed contract, and invest without verifying that the audited code matches the actual deployed contract. This verification takes one step: compare the contract code hash in the audit report to the code hash displayed on Etherscan for the actual deployed address. If they differ, the audit is irrelevant to the contract you are investing in.
The audit firm's reputation also matters enormously. The market for crypto audits includes established firms like CertiK, Trail of Bits, Consensys Diligence, and OpenZeppelin, alongside dozens of low-cost outfits that produce audit reports of minimal analytical value. A "clean audit" from an unknown firm with no track record and a suspiciously short turnaround time provides almost no real security assurance. CertiK itself has faced criticism for awarding high security scores to projects that subsequently failed, illustrating that even reputable auditors work from the information they are given and cannot guarantee the team's future behavior.
The correct mental model for audits: an audit reduces the probability of unintentional code bugs causing losses. It does not reduce the probability of intentional developer fraud causing losses. Both risks exist independently.
These terms describe the same fundamental betrayal at different speeds, and the distinction matters for recognizing slower-moving scams that do not match the dramatic overnight collapse that "rug pull" usually evokes.
A hard rug is the catastrophic, rapid exit that this article primarily describes. The liquidity pool is drained in a single transaction. The price crashes 99% in minutes. Developers delete all communication channels and disappear simultaneously. The entire event is over in under an hour, often faster. Hard rugs are unambiguous and immediately recognizable.
A soft rug is a gradual abandonment where developers slow-walk the exit over weeks or months. Development activity slows and eventually stops. Social media posts become infrequent and vague. Promised roadmap milestones keep getting delayed without explanation. The team becomes increasingly unresponsive to community questions. Meanwhile, the team may be slowly offloading their token holdings in small increments to avoid triggering a panic, each individual sale small enough not to crash the price but collectively representing their exit from the project.
Soft rugs are harder to detect precisely because there is always a plausible alternative explanation for each individual signal. Maybe development is slow because the team is being careful. Maybe the social media silence is because they are heads-down on a feature. The manipulation is built into the ambiguity. The on-chain signal that cuts through the ambiguity is developer wallet activity: if team wallets are consistently selling small amounts into any price strength over several weeks, the soft rug is in progress regardless of what the team says publicly. Tracking developer wallet addresses, set up as alerts through Wallet Finder.ai or a similar platform, converts this slow-moving signal into a concrete notification you can act on before the final exit.
The terms are sometimes used interchangeably but describe meaningfully different mechanics with different risk profiles and different optimal defenses.
A pump and dump is primarily a price manipulation scheme. A group acquires a token or stock at a low price, then aggressively promotes it to drive buying demand from outside investors, then sells their accumulated position into the rising price. The underlying project may be real or may be a complete fiction, but the defining characteristic is that the manipulators' goal is to sell into elevated price, not necessarily to steal the underlying liquidity or prevent selling. After the dump, the token still exists. Its price crashes, but it is still tradeable. Outside investors can still sell, they just sell at a massive loss.
A rug pull involves direct theft from the protocol's infrastructure itself, specifically the liquidity pool or the smart contract's holdings. The token may become permanently untradeable after a liquidity pull because there is no ETH left in the pool to swap against. The distinction matters because pump and dump victims have actually sold their tokens at a bad price, whereas hard rug pull victims may find themselves holding tokens that literally cannot be sold for any price because the market mechanism for doing so has been destroyed.
The defensive response to each differs accordingly. Against pump and dump risk, the primary defense is avoiding assets with suspicious promotional patterns and setting realistic profit-taking targets rather than holding through extreme price appreciation. Against rug pull risk, the primary defense is the smart contract and liquidity analysis described throughout this article, because the vulnerability is structural and detectable before the event occurs rather than only recognizable after the price has already moved.
Ready to turn raw blockchain data into a real trading advantage? Wallet Finder.ai is built to help you track smart money, dig into developer wallets, and catch suspicious activity before it’s too late. See what the top traders are doing in real time and protect your capital.