Best Wallet Tracker Tools for DeFi Traders in 2026
Discover the best wallet tracker for DeFi in 2026. Compare 12 top tools like Wallet Finder.ai to find, track, and copy smart money wallets.

February 12, 2026
Wallet Finder

January 20, 2026

Think of a security auditing service as a SWAT team for your code. You're hiring expert, ethical hackers to storm your digital fortress, find every crack and weakness, and report back before real attackers get a chance. This deep dive is critical for keeping software safe, especially in the high-stakes world of DeFi where a single bug can cost millions.
You wouldn't buy a house just by looking at the Zillow pictures, right? You'd hire a professional inspector to crawl through the attic and check the foundation for hidden problems. A security auditing service does the exact same thing for a DeFi protocol or smart contract. It’s an independent, expert review designed to uncover hidden flaws that could put user funds at risk.
Without this step, projects are basically launching with a "hope for the best" strategy. It's like a house with faulty wiring just waiting to start a fire. For traders, an audit report is one of the most fundamental pieces of due diligence you can do. It cuts through the hype and gives you a real, tangible measure of a team's commitment to protecting your money.
A proper security check-up isn't a one-and-done deal. It's a comprehensive process that looks at a project from multiple angles, usually covering three distinct layers of its architecture. Understanding these pillars helps you see the full picture of what’s being protected.
These services are a huge and growing market for a reason. The demand for rock-solid security is exploding, with the Cybersecurity Audit Services Market valued at USD 14.5 billion in 2024. It's projected to hit a massive USD 39.8 billion by 2032, growing at a 12.5% CAGR. This just goes to show how vital audits are for preventing hacks, much like how Wallet Finder.ai helps traders sidestep risky wallets by surfacing smart money moves. You can explore more data on this expanding market to see the trend for yourself.
To help you make sense of it all, here's a quick breakdown of what goes into a typical crypto security audit.
This table sums up the main types of audits you'll encounter in DeFi, what they focus on, and why they should matter to you as a trader or investor.
Each audit type covers a different potential attack surface, and together, they provide a much more complete assessment of a project's security.
A security audit is not a one-time "pass or fail" test. It's a collaborative process of discovery and remediation where auditors identify issues and the development team works to fix them, strengthening the project for everyone.
By combining these three approaches, a thorough security auditing service gives you a much clearer, more reliable picture of a project's overall resilience. It’s the kind of confirmation you need before you can confidently put your capital to work.
A professional security audit isn't a black box where code goes in and a report magically appears. It's a structured, multi-stage process where sharp human expertise and powerful tools team up to pick apart a protocol's defenses. Understanding this journey shows why a real audit is so much more than a quick once-over.
Think of it like a military special ops team planning a mission. They don't just charge in. They gather intel, map the terrain, probe defenses, and then execute a precise plan. A top-tier security auditing service uses a similarly disciplined methodology to make sure nothing is left to chance.
This flow chart breaks down the core stages of a comprehensive crypto security audit, from digging into the smart contracts to testing the infrastructure and running penetration tests.
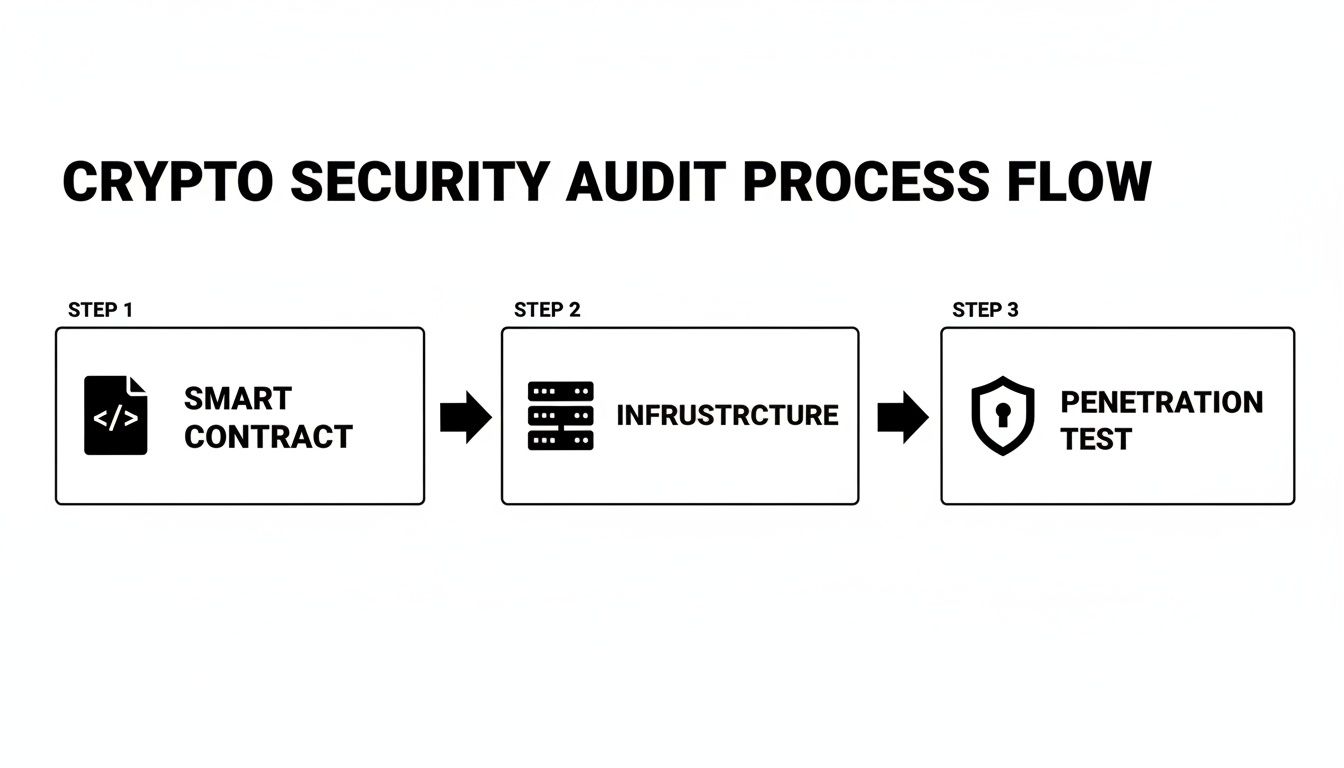
As you can see, a complete audit hits multiple layers of a project, not just the code living on the blockchain. This holistic view is crucial for getting a true sense of the risks involved.
Here is a breakdown of the typical stages in a professional security audit:
Phase 1: Scoping and Information Gathering
The audit kicks off with a deep dive into the project's architecture, documentation, and intended functionality. Auditors get full "whitebox" access, meaning they see all source code and system details. During this stage, the auditors and the project team agree on the exact scope, defining which smart contracts and off-chain components are to be reviewed.
Phase 2: Automated Scanning
The first wave of analysis uses automated tools to flag common, "low-hanging fruit" vulnerabilities. These programs scan the code for patterns matching known bugs or poor coding practices. This step is efficient but serves as a preliminary check, clearing the way for deeper, manual analysis.
Phase 3: Manual Code Review
This is the heart of the audit. Seasoned security engineers manually review every line of code. They hunt for subtle logic flaws, potential economic attacks, and architectural weaknesses that automated tools miss. The engineers focus on high-risk areas like access controls, reentrancy vulnerabilities, and integer overflows.
Phase 4: Vulnerability Exploitation (Penetration Testing)
After spotting potential weaknesses, auditors attempt to exploit them in a safe, controlled test environment. This proves whether a theoretical vulnerability is practically exploitable and demonstrates its potential impact, making the threat tangible for the development team.
Phase 5: Reporting and Remediation
All findings are compiled into a detailed audit report. Each vulnerability is assigned a severity rating (e.g., Critical, High, Medium) and includes clear, actionable remediation steps. The auditors then work with the dev team to ensure the fixes are implemented correctly and effectively resolve the issues.
The manual review is where an auditor's experience really shines. They look at the code through an attacker's eyes, constantly asking, "How can I make this protocol do something it's not supposed to do?"
A security audit report can look intimidating, but you don’t need to be a developer to extract the critical insights. Think of it like reading a nutrition label; you just need to know where to look. By focusing on four key sections, you can quickly assess a project's risk profile and make informed decisions.
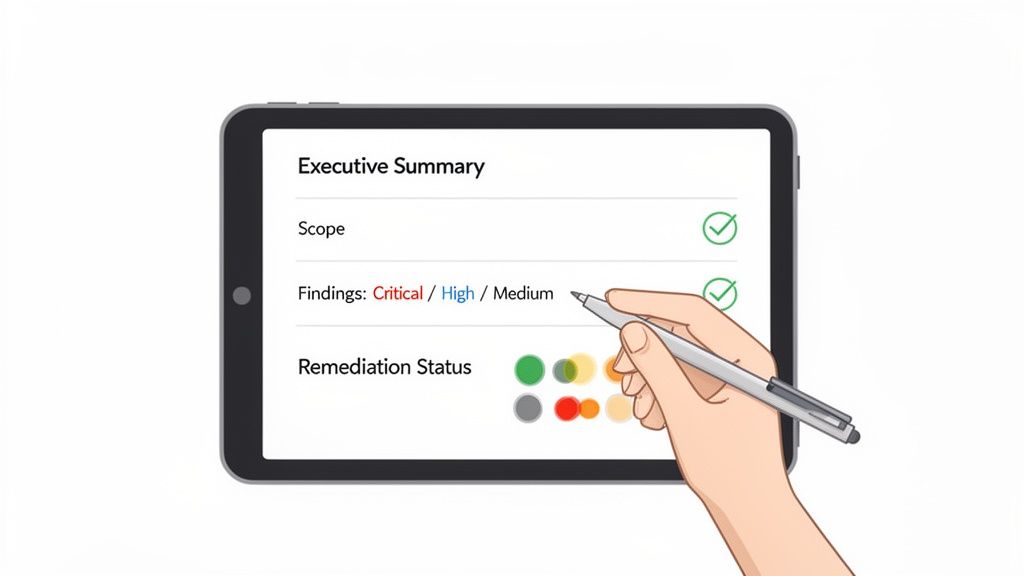
The Executive Summary is your top-level briefing. It’s written for a non-technical audience, giving you the auditors' overall verdict in plain English. This section summarizes the most important findings and gives a general feel for the code's quality and the team's security mindset. Pay close attention to the tone here. Is it confident and professional? Or does it use cautious language that hints at deeper issues?
Next, jump straight to the Scope section. This is arguably one of the most important parts of the whole document because it tells you exactly what was tested—and more importantly, what wasn't. A project might brag about a "clean audit," but if that audit only covered a single, non-critical smart contract, the claim is basically worthless. Look for a clear list of the specific smart contract addresses or code repositories that were actually reviewed.
This is the real meat of the report. The Findings section breaks down every single vulnerability the auditors uncovered, usually sorted by how dangerous it is.
A report with zero critical or high findings is obviously a great sign. But don't just count the number of issues; look at the types of problems found. Repeated findings of the same bug class can signal systemic weaknesses in the development process.
A project with several critical vulnerabilities that are all marked as "Fixed" can be a stronger sign of a competent team than a project with a "clean" report that had a very narrow scope. It shows the team takes security seriously and knows how to respond to feedback.
The final, and most critical, step is checking the Remediation Status. This section tells you if the project’s developers actually fixed the problems the auditors found.
Look for a status next to each finding:
Use this quick checklist every time you look at a project's security audit to focus on what truly matters.
By running through this checklist, you can quickly move beyond the marketing hype and get an honest assessment of a protocol's security.
Not all audits are created equal. When it comes to something as critical as a security auditing service, the firm’s reputation is just as important as the final report they hand over. Picking the right auditor can be the difference between a secure, trusted protocol and becoming the next major hack.
The first place to look is their history. Any auditor worth their salt will have a public portfolio showcasing the projects they’ve secured. But don’t just glance at the logos on their homepage. Dig in. Read the actual reports they’ve published for well-known and successful DeFi protocols. You want to see firms that have audited projects with similar complexity and scope to the one you’re looking at.
A strong portfolio isn't just a list of clients; it's a library of evidence. It shows a firm's ability to find critical vulnerabilities and a history of being trusted by teams that take security seriously.
A great security auditing service is nothing without its engineers. Look for firms that are transparent about their team’s background. You want to see seasoned experts with a history in cybersecurity, reverse engineering, and hands-on smart contract development. Their process matters, too. A good firm will have a clear, well-documented methodology that always involves a mix of automated scanning tools and an intense manual review by human experts.
The crypto security community is a small, tight-knit world. A firm’s reputation within this circle is one of the best indicators of its quality. Do their researchers publish interesting findings? Do they compete in Capture The Flag (CTF) events? A good reputation is earned, not bought. It comes from consistently delivering high-quality work and actively participating in making the ecosystem safer.
This table breaks down the key signs to look for when you're sizing up a potential security auditor.
In the end, choosing a security auditing service is about finding a true partner, one genuinely committed to making a project safer.
A report from a security auditing service is an essential piece of the puzzle, but it's not the whole picture. An audit is like a home inspection: it checks the foundation to ensure everything is built to code. It's a critical, non-negotiable step. But that inspection won't tell you about the neighborhood. For that, you need to watch what's happening in real time.
That's where on-chain intelligence comes in. Smart traders know that a static code review is only half the story. The real narrative of a protocol unfolds live on the blockchain. Combining a solid audit with on-chain data gives you a powerful, two-pronged approach to managing risk.

An audit confirms the foundation is solid. On-chain tools show you what the smart money is actually building on top of it.
An audit is your starting point. It's the foundational layer of trust, verifying that the code isn't a complete mess of obvious vulnerabilities. A project without a reputable audit is like a ship setting sail with visible holes in its hull—you just don't get on board.
The audit answers critical questions:
If the answers aren't a confident "yes," then there's no point in digging any deeper.
While an audit examines the code's potential, on-chain data reveals its reality. It shows you how the most informed players in the market are interacting with the protocol right now. Tools like Wallet Finder.ai are designed to translate raw, messy blockchain data into signals you can actually use. They let you see if smart money is piling into a project's token after a good audit, or if the team members are quietly dumping their bags.
An audit report is a project's resume; it lists its qualifications and experience. On-chain data is the live job interview, showing you how it actually performs under pressure.
Here’s a simple workflow for integrating these two powerful data sources:
By layering dynamic, real-time wallet activity on top of a static code review, you stop being a reactive investor and become a proactive one. You can learn more about how to interpret these signals in our guide to understanding crypto on-chain analysis.
A real, in-depth audit is a serious investment in both time and money. The cost and timeline shift dramatically based on how big and complicated your project is. A basic ERC-20 token might only take a week, but a complex DeFi protocol with brand-new financial mechanics could easily tie up a team of engineers for a month or more.
When an auditing firm gives you a quote, they're pricing out the expert hours needed to analyze your project.
Here’s what they’re looking at:
If an audit sounds too cheap or too fast, it’s a massive red flag. Quality security work is done by highly specialized engineers whose time is in high demand. Expect a legitimate smart contract audit to start at $10,000 and go up significantly from there.
This is the single most important thing to understand: a clean audit is not a certificate of absolute safety. It's a risk reduction tool, not a magic shield. Thinking an audit makes a project invincible is a recipe for disaster. An audit is a snapshot in time.
Here are a few things an audit will not protect you from:
The demand for security services is only getting bigger, with the global Security Audits and Assessments Market expected to reach USD 16.42 billion by 2030. This market intelligence report highlights a shift toward subscription models, which is something we also see at Wallet Finder.ai with our flexible trial and subscription plans. By understanding what an audit is really for—finding code-level risks—you can use its findings as one part of a much larger due diligence strategy.
Diving into crypto security can feel like a minefield. Let's clear up some of the most common questions people have about security auditing services.
Yes, and this is a critical point to understand. An audit is a massive step in the right direction for security, but it's not a magic shield. Think of it as a deep, expert inspection that significantly reduces the chance of a hack by rooting out known vulnerabilities.
But here’s the reality: new, creative ways to attack protocols are discovered all the time. The very best auditors can’t predict the future. Plus, a project’s security is bigger than just its smart contracts. A hack could happen if a team member's private keys are stolen or if a connected third-party service gets compromised—things completely outside the audit's scope.
An audit is a huge green flag, but it's just one part of your research. Never treat it as a 100% guarantee of safety.
They're both essential for security, but they serve different purposes and operate at different times. It’s like the difference between an architect reviewing blueprints and having 24/7 security guards on patrol.
Security Audit: This is a proactive, deep dive into a project's code before it launches or undergoes a major upgrade. A specialized firm is hired for a set period to methodically hunt for flaws and provide a foundational security check-up.
Bug Bounty: This is an ongoing, reactive security program for a live project. The team offers cash rewards to any ethical hacker in the world who finds and reports a vulnerability. It’s continuous, crowd-sourced security.
A project that has both an audit and a bug bounty program is showing a serious commitment to keeping user funds safe.
Security isn't a one-and-done deal; it's a process. At a minimum, every DeFi protocol needs a full audit before its initial launch on mainnet.
From that point on, a new audit is absolutely essential after any significant upgrade or change to the core smart contracts. Even what seems like a minor tweak can introduce a catastrophic bug. For established protocols, it's also a best practice to get re-audited periodically (say, once a year) to check the existing code against newly discovered attack methods. It’s just good security hygiene.
Ready to combine audit insights with real-time on-chain intelligence? Wallet Finder.ai helps you track smart money movements and see how top traders react to newly audited projects. Start your free 7-day trial and turn data into an advantage at https://www.walletfinder.ai.