Best Wallet Tracker Tools for DeFi Traders in 2026
Discover the best wallet tracker for DeFi in 2026. Compare 12 top tools like Wallet Finder.ai to find, track, and copy smart money wallets.

February 12, 2026
Wallet Finder

February 11, 2026

Navigating the market for security audit software can be a formidable task. Organizations face a critical need to identify and remediate vulnerabilities across complex environments, from on-premise networks and cloud infrastructure to sophisticated web applications and decentralized finance (DeFi) protocols. The right tools automate this process, providing the visibility and control necessary to maintain a strong security posture and meet stringent compliance mandates. Without effective software, security teams are left manually sifting through potential threats, a slow and error-prone approach that leaves critical assets exposed.
This guide is designed to cut through the noise. We provide a comprehensive, curated roundup of the top security audit software solutions available today. Whether you are a startup building your first application, a large enterprise managing a sprawling network, or a developer securing smart contracts, this resource will help you find the best tool for your specific needs. We’ll move beyond marketing jargon to offer an honest assessment of each platform's strengths and weaknesses.
In the following sections, you will find detailed analysis covering:
This listicle serves as your direct path to selecting the most effective security audit software, saving you hours of research and helping you build a more resilient security foundation.
Tenable is a cornerstone in the cybersecurity industry, renowned for its foundational vulnerability scanning and management platforms. It offers a suite of tools, from the iconic Nessus scanner to the cloud-based Tenable Vulnerability Management, designed for comprehensive infrastructure and web application security auditing. This platform excels at providing deep visibility into your entire attack surface, making it an essential piece of security audit software for organizations aiming to identify and prioritize vulnerabilities before they can be exploited.
Tenable’s strength lies in its extensive and continuously updated plugin library, which detects thousands of misconfigurations, malware, and vulnerabilities across a wide range of operating systems, devices, and applications. The platform’s robust compliance and configuration auditing capabilities allow teams to benchmark systems against standards like CIS and DISA STIGs, streamlining regulatory adherence.
Pros:
Cons:
Website: https://www.tenable.com/buy
Rapid7 InsightVM is a modern vulnerability risk management platform designed to provide live visibility and actionable insights across complex hybrid environments. As a comprehensive piece of security audit software, it combines agent-based and agentless scanning to cover everything from on-premises servers to cloud instances and containers. The platform moves beyond simple vulnerability detection by incorporating threat intelligence and real-world attack data to prioritize risks, helping security teams focus on what matters most.
InsightVM's key differentiator is its "Attacker's-Eye View," which helps teams understand how vulnerabilities could be chained together in an attack. It integrates directly into developer and IT workflows, with ticketing system connections that automate remediation tasks and track progress. This emphasis on workflow integration makes it a practical choice for organizations looking to operationalize their vulnerability management program rather than just generating static audit reports. For organizations seeking external expertise, many security audit services use similar tools to conduct their assessments.
Pros:
Cons:
Website: https://www.rapid7.com/products/insightvm/
Qualys VMDR stands out as a comprehensive, all-in-one cloud platform that consolidates vulnerability management, detection, and response. It moves beyond simple scanning by integrating asset discovery, prioritized threat intelligence with its TruRisk scoring, and built-in patching capabilities into a single workflow. This unified approach makes it a powerful piece of security audit software for organizations seeking to not only identify vulnerabilities but also to streamline the entire remediation lifecycle from a central console.
The platform’s strength is its lightweight, universal Cloud Agent, which provides continuous, real-time visibility into asset health without the need for constant network-based scanning. Qualys VMDR leverages this data to create a global IT asset inventory, detect security gaps, and automate patching for operating systems and third-party applications. Its modular design allows businesses to add capabilities like patch management, compliance monitoring, and web application scanning as their needs evolve.
Pros:
Cons:
Website: https://www.qualys.com/solutions/vmdr/
Invicti, which incorporates the well-known Acunetix scanner, is a powerful player in the web application security space, focusing on dynamic application security testing (DAST) combined with optional interactive application security testing (IAST). It's designed for organizations that need to secure a large portfolio of websites, web applications, and APIs without being penalized for scale. This platform distinguishes itself as a premier piece of security audit software by offering an unlimited scanning model, which is a significant advantage for development-heavy environments.
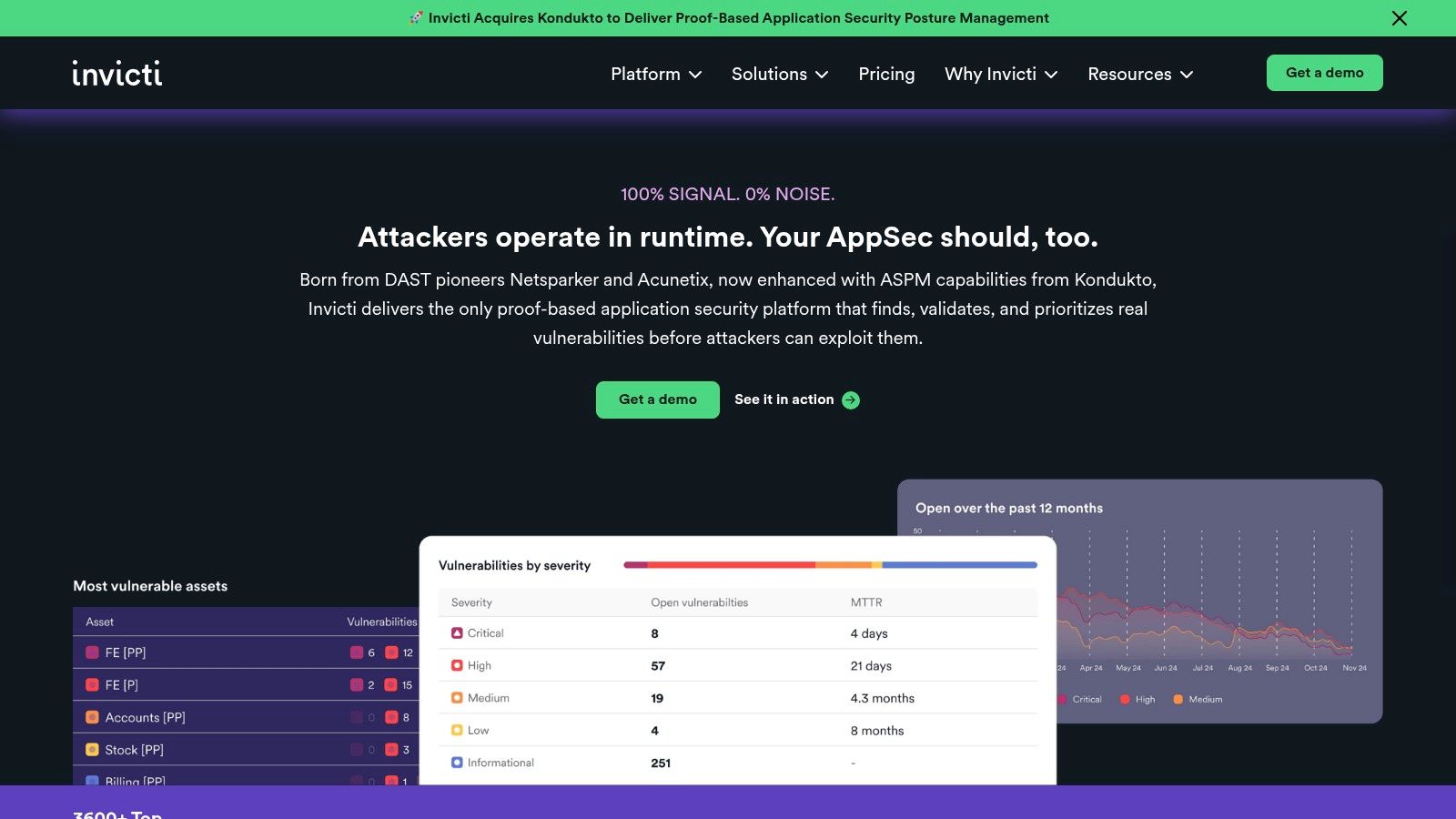
The core strength of Invicti lies in its "Proof-Based Scanning" technology, which automatically confirms the exploitability of many detected vulnerabilities, drastically reducing the time security teams spend on manual verification. This focus on accuracy and automation makes it highly effective for integration into CI/CD pipelines, enabling a true DevSecOps approach where security checks are a seamless part of the development lifecycle. This automation is also a critical component in broader security strategies, similar to how automated monitoring is essential for smart contract security post-deployment.
Pros:
Cons:
Website: https://www.invicti.com/
PortSwigger's Burp Suite is the definitive toolkit for hands-on web application security testing. Widely regarded as the industry standard for penetration testers and application security professionals, it combines an intercepting proxy with a powerful suite of manual and automated tools. This platform is essential security audit software for anyone performing in-depth analysis of web traffic and hunting for complex vulnerabilities that automated scanners might miss.
Burp Suite excels at giving security auditors granular control over HTTP/S requests, allowing them to manipulate, replay, and analyze traffic to uncover flaws. Its Enterprise edition extends this capability into an automated DAST solution that integrates with CI/CD pipelines, enabling organizations to scale their security testing efforts. A comprehensive understanding of website security audits often involves using tools like Burp Suite for both manual validation and automated scanning.
Pros:
Cons:
Website: https://portswigger.net/burp/
Greenbone represents a powerful intersection of open-source heritage and commercial-grade vulnerability management. Stemming from the well-known OpenVAS project, Greenbone offers a comprehensive security audit software suite that scales from free, community-supported tools to robust, enterprise-ready physical and virtual appliances. This dual approach makes it an excellent choice for organizations seeking powerful scanning capabilities without the high entry costs often associated with purely commercial solutions.
The platform's core strength is its extensive feed of Network Vulnerability Tests (NVTs), which covers a vast range of enterprise software, network devices, and operating systems. Greenbone provides deep asset discovery, automated scanning, and detailed reporting, allowing security teams to manage the entire vulnerability lifecycle. Its flexible deployment models cater to different needs, from on-premises control to subscription-based services.
Pros:
Cons:
Website: https://www.greenbone.net/
ManageEngine ADAudit Plus is a specialized security audit software focused squarely on Windows environments, offering comprehensive auditing of Active Directory (AD), Azure AD, and Windows servers. It provides security teams and system administrators with granular visibility into all changes happening across their AD infrastructure. This tool is critical for maintaining security posture, troubleshooting operational issues, and generating the specific evidence required for compliance audits.
The platform excels at translating complex, raw event log data into easy-to-understand reports and real-time alerts. Instead of manually sifting through logs, ADAudit Plus presents clear information on who made what change, from where, and when. Its strength lies in this deep focus on the Microsoft ecosystem, making it an indispensable tool for organizations heavily reliant on Active Directory for identity and access management.
Pros:
Cons:
Website: https://www.manageengine.com/products/active-directory-audit/
SolarWinds Security Event Manager (SEM) is a Security Information and Event Management (SIEM) platform designed for centralized log collection, correlation, and compliance reporting. While not a traditional scanner, it is crucial security audit software for creating a comprehensive audit trail. By aggregating log data from servers, network devices, and endpoints, SEM provides the visibility needed to detect threats, investigate incidents, and produce evidence for compliance audits like PCI DSS, SOX, and HIPAA.
The platform's strength lies in its ability to normalize disparate log formats and apply real-time correlation rules to identify suspicious activity that isolated tools might miss. Its agent-based and agentless data collection methods offer flexibility, and its deployment as a virtual appliance simplifies setup. This makes SEM a practical choice for organizations needing to consolidate security monitoring and streamline audit preparation without a heavy hardware footprint.
Pros:
Cons:
Website: https://www.solarwinds.com/security-event-manager
Wazuh is a powerful, open-source security platform that combines Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) capabilities. It provides a unified solution for threat detection, integrity monitoring, incident response, and compliance, making it a highly versatile piece of security audit software. The platform is designed to collect, aggregate, and analyze security data from across an organization's infrastructure, offering deep visibility into security events on endpoints, cloud services, and containers.
What makes Wazuh stand out is its open-source nature, offering a completely free, self-hosted option for teams with the technical expertise to manage it. For those seeking a more hands-off approach, Wazuh Cloud provides a fully managed SaaS solution. This flexibility allows organizations of all sizes to leverage enterprise-grade security monitoring and auditing tools without the hefty price tag often associated with commercial SIEM/XDR products.
Pros:
Cons:
Website: https://wazuh.com/
The Center for Internet Security (CIS) offers the CIS SecureSuite, a product family centered around its globally recognized security best practices, the CIS Benchmarks. This suite is essential for organizations focused on compliance and secure configuration hardening, providing the tools needed to assess and enforce these standards across their infrastructure. The primary tool, CIS-CAT Pro, automates the process of auditing systems against these benchmarks, making it a cornerstone piece of security audit software for achieving a strong, standardized security posture.
CIS SecureSuite’s authority comes from its consensus-developed benchmarks, which serve as the de facto standard for secure configurations for over 100 technologies. CIS-CAT Pro allows IT and security teams to scan assets, score them against these benchmarks, and receive actionable guidance for remediation. This capability is invaluable for demonstrating compliance with frameworks like PCI DSS, HIPAA, and NIST, as CIS Benchmarks are often a required configuration standard.
Pros:
Cons:
Website: https://www.cisecurity.org/cis-securesuite/
AWS Marketplace is not a single tool but a centralized digital catalog where organizations can find, test, buy, and deploy third-party security audit software that runs on Amazon Web Services. It streamlines procurement by consolidating billing through your existing AWS account and offering flexible pricing models, including free trials, hourly, and annual subscriptions. For teams deeply integrated with the AWS ecosystem, it's the most efficient way to acquire and manage security tools from leading vendors.
The platform’s key advantage is simplifying the discovery and deployment of everything from vulnerability scanners and static analysis tools to comprehensive security assessment services. Its Vendor Insights feature provides a dashboard for reviewing a vendor's security and compliance posture, helping you vet solutions before purchase. This makes the Marketplace an essential resource for sourcing pre-approved and easily deployable security audit software.
Pros:
Cons:
Website: https://aws.amazon.com/marketplace/
Netwrix Auditor is a specialized IT audit software platform focused on providing deep visibility into changes, configurations, and access across critical IT systems. Unlike vulnerability scanners, its primary function is to answer the "who, what, when, where" of user activity, making it an indispensable tool for security audits centered on compliance, insider threat detection, and operational integrity. The platform excels at consolidating audit trails from disparate sources like Active Directory, file servers, Microsoft 365, and databases into a single, searchable interface.
The core strength of Netwrix Auditor lies in its comprehensive reporting and alerting capabilities. It provides pre-built reports mapped directly to compliance standards such as PCI DSS, HIPAA, and SOX, significantly reducing the manual effort required for audit preparation. By monitoring critical changes and access events in real-time, it helps security teams quickly detect and respond to suspicious activities that could indicate a security breach or policy violation.
Pros:
Cons:
Website: https://www.netwrix.com/en/products/auditor/
Throughout this guide, we have explored a diverse range of powerful security audit software, from comprehensive vulnerability management platforms like Tenable and Rapid7 InsightVM to specialized web application scanners such as Invicti and Burp Suite. We've seen how tools like ManageEngine ADAudit Plus and Netwrix Auditor excel at monitoring internal changes, while open-source solutions like Wazuh and OpenVAS provide accessible starting points for organizations of all sizes. The key takeaway is clear: a proactive audit is the non-negotiable foundation of any robust security posture.
However, for participants in the fast-paced world of DeFi and on-chain asset management, a static audit is only half the battle. The digital landscape, particularly the blockchain, is not a fixed environment. It is a dynamic ecosystem where new threats, smart contract interactions, and exploits emerge in real time. An audit performed last week cannot protect you from a zero-day exploit discovered today or a sophisticated phishing attack targeting a protocol you actively use. This is where the paradigm must shift from periodic check-ups to continuous vigilance.
The core limitation of any traditional security audit software is its "point-in-time" nature. It provides an essential, detailed snapshot of your vulnerabilities at the moment of the scan. While invaluable for patching known weaknesses, this approach leaves a critical gap: the time between audits. In DeFi, this gap can be a window of immense opportunity for attackers.
To close this gap, you must augment your audit strategy with real-time, on-chain monitoring. Think of it this way:
Combining these two approaches creates a comprehensive security lifecycle. You use audit tools to harden your systems and then deploy monitoring solutions to watch for threats in the wild that could bypass those hardened defenses. This dual-layered strategy transforms security from a passive checklist into an active, intelligent defense mechanism.
Choosing the right security audit software is the critical first step. Your decision should be guided by your specific context, whether you're a startup, a large enterprise, or a DeFi project team.
How to Choose Your Tools:
Once your foundational audit process is in place, the next immediate action is to layer on real-time threat intelligence. For anyone operating on-chain, this means tracking the flow of smart money, monitoring high-performing wallets for signs of exploits, and staying ahead of market-moving events. This is not a function of traditional audit software; it requires a specialized on-chain intelligence platform. By integrating periodic deep-dive audits with constant on-chain surveillance, you build a truly resilient defense that protects your digital assets before, during, and after any potential threat emerges.
While security audit software hardens your own systems, true alpha in DeFi comes from understanding and anticipating the on-chain actions of others. Wallet Finder.ai provides the critical real-time monitoring layer, allowing you to track smart money, discover top trader wallets, and receive instant alerts on suspicious activity. Go beyond static audits and gain a proactive edge by exploring the power of on-chain intelligence at Wallet Finder.ai today.