Guide to Lone Wolf Transactions in DeFi
Discover how lone wolf transactions signal smart money moves. Learn to find and analyze these elite solo traders to sharpen your own DeFi strategy.

February 15, 2026
Wallet Finder

February 7, 2026

A security audit network isn't a single company; it's an ecosystem of experts, tools, and processes working together to ensure a DeFi project is safe. Think of it as a multi-layered inspection team giving a protocol's digital foundation a thorough shakedown before anyone puts real money into it.
Imagine you're investing in a new skyscraper. You wouldn't just take the architect's word that it's safe. You'd expect a team of independent inspectors to verify everything: one crew checks the structural integrity (the code), another examines the electrical and plumbing (the network infrastructure), and a third simulates fires or earthquakes (economic exploits).
The security audit network does exactly that for DeFi protocols.
For a trader, jumping into a project based on marketing hype without checking its audit is like buying a condo in that skyscraper from a glossy brochure. You're ignoring the blueprints and stress tests that reveal whether it's stable or a disaster waiting to happen.
Learning to read and interpret the findings from this network is your most powerful line of defense. It allows you to look past flashy metrics and see the real, often hidden, risks buried in the code. This guide teaches you how to read those blueprints, so you can tell a solid project from one with dangerous cracks in its foundation.
A comprehensive security audit has several key parts:
Ultimately, a strong security audit network signals that a project cares about keeping user funds safe. Using the work done by a professional security auditing service is a non-negotiable skill for anyone serious about protecting their capital. It changes you from a passive investor into a sharp analyst who can make much smarter, safer decisions.
A thorough security audit isn't a single event; it's a multi-faceted investigation. To truly understand a protocol's resilience, you must move beyond asking, "Is it audited?" The real question is, "How was it audited?"
This means digging into the four distinct pillars that form a complete security profile. Understanding these gives you a powerful framework for judging how seriously a project takes protecting user funds. It helps you see the whole picture, from the code running on the blockchain to the off-chain systems that keep everything humming.
This holistic approach, shown below, combines the sharp eyes of human auditors, the raw power of specialized tools, and the discipline of defined processes to create a robust defensive ecosystem.
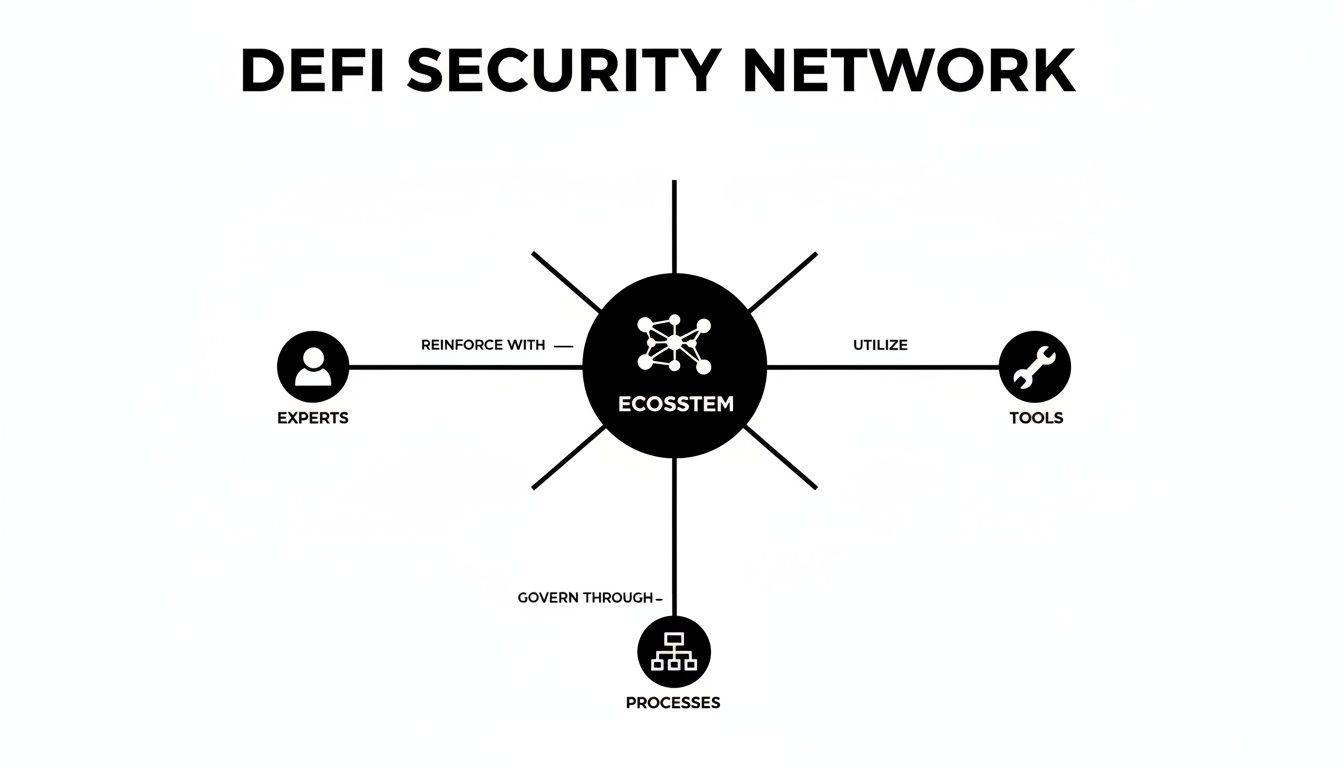
As you can see, a strong security audit network isn't about one thing—it’s an interconnected system where experts, tools, and processes all work in concert to fortify the DeFi space. Each element makes the others stronger.
This is the most well-known pillar. A smart contract audit is a line-by-line inspection of the protocol's on-chain code—the logic that handles every transaction and holds all assets. Auditors meticulously hunt for common but devastating bugs like reentrancy, integer overflows, and access control flaws that hackers love to exploit.
A single vulnerability in a smart contract can lead to a catastrophic, total loss of user funds. This makes the smart contract audit the absolute, non-negotiable foundation of any project's security claims.
This process involves a mix of automated scanning tools and, crucially, manual expert review. The goal is to sniff out any logical error or vulnerability that could be manipulated. You can get the full rundown in our deep dive on smart contract security best practices.
While smart contracts live on the blockchain, most DeFi protocols rely on off-chain components to function. Network and infrastructure audits zero in on these critical support systems. These include:
A weak spot here—say, a compromised API or a manipulated price oracle—can be just as destructive as a bug in the smart contract itself. This pillar ensures the entire operational stack is buttoned up.
This is the most rigorous, mathematically intense form of security analysis. Instead of just looking for bugs, formal verification aims to create a mathematical proof that the code behaves exactly as intended under every conceivable condition. Think of it as proving, with absolute certainty, that a bridge's design will never fail, no matter the load. That’s what formal verification does for code. Because it's so complex and expensive, it's usually reserved for only the most critical, high-value parts of a protocol.
The final pillar harnesses the power of the global security community. A bug bounty program offers cash rewards to ethical hackers who find and responsibly report vulnerabilities that internal and external audit teams might have missed. This creates a continuous, crowdsourced audit, giving thousands of skilled researchers a real incentive to pick apart a project's code and providing an ongoing layer of defense that evolves as new attack methods emerge. Projects with generous and active bug bounty programs signal a strong, long-term commitment to keeping users safe.
Each type of audit plays a unique and critical role. While they can overlap, their primary focus and methods are distinct. The table below compares them side-by-side.
Ultimately, a project that invests in all four pillars is demonstrating a deep, layered commitment to security. It's a clear signal they aren't just checking a box—they're building a fortress.

Opening a security audit report can feel like trying to read a different language, packed with technical jargon. But here’s the secret: you don’t need to be a developer to pull out the most important signals. Learning to navigate these documents is a powerful research skill. Here’s a step-by-step process to extract actionable intelligence.
Every good audit report kicks off with an executive summary. This is your home base. It’s the high-level briefing of the audit’s scope, methods, and—most importantly—the big-picture findings.
Pay attention to these key elements:
An executive summary is the 30,000-foot view. It should tell you whether the auditors found a well-built fortress with a few minor cracks or a crumbling structure held together with duct tape.
After reading it, you should have a solid gut feeling about the project's security posture. This section sets the stage for everything that follows and gives context to the work done by the security audit network that performed the review.
Auditors categorize findings by how dangerous they are. Understanding this hierarchy helps you separate signal from noise.
Here’s a typical breakdown of what you'll see:
This is the most important part. Finding bugs is one thing; what the team does about them is everything. A good audit report tracks the solution for each problem. Scan the report for the status of each finding.
Here’s what to look for:
Put on your detective hat here. A team that meticulously fixes every single issue is showing you they have a security-first mindset. A team that shrugs off major warnings from the security audit network is telling you loud and clear that your funds are not their top priority.
Seeing that shiny "Passed Audit" badge on a project's website can give a dangerous false sense of security. To protect your portfolio, you need to be skeptical and think like a risk manager. Many audits contain hidden gaps that most traders completely miss. Learning to see past the marketing hype is a critical skill.
One of the most common tricks is the scope limitation. Think of it like hiring a home inspector who is only allowed to look at the living room. They might give it a perfect score, but that tells you nothing about the faulty wiring in the basement.
This happens all the time in DeFi. A project will get a single, non-critical smart contract audited and then plaster "Audited" all over their marketing, implying the entire protocol is secure.
Actionable Tip: Always jump straight to the audit's scope section. Find out exactly which contracts and components were reviewed. If the core logic that holds user funds was left out, the audit is practically useless.
Another big red flag is auditor shopping. This is when a project, often knowing it has security issues, deliberately seeks out less experienced or less reputable auditing firms. They aren't looking for a real security check; they're shopping for an easy pass.
Actionable Tip: If you see an audit from a firm you've never heard of, do your homework. A true security audit network is built on firms with long, public track records like Trail of Bits and OpenZeppelin. An unknown auditor is a major warning sign.
An audit is a snapshot in time, not a lifetime guarantee of security. A report from last year means very little for a protocol that has pushed major updates since then.
This is a crucial point. Code is constantly changing. Every new feature can introduce a brand-new vulnerability. Always check the date of the audit and compare it to the project's development timeline. An old audit for a fast-moving protocol is as good as no audit at all.
Even a solid audit can miss brand-new threats. A recent Global Digital Trust Insights survey by PwC.com highlights that knowledge gaps are a massive challenge. While 64% of organizations now check their AI tools for security flaws, this is a recent trend. Older audits almost certainly ignored AI-driven attack vectors. This matters when cloud intrusions are up 75% year-over-year. These new threats can punch huge holes in a project's security if they aren't specifically addressed in recent, comprehensive audits.
Ultimately, treat an audit report as just one piece of evidence in a larger investigation. You can learn more about specific code-level flaws in our guide on detecting reentrancy attacks and other common exploits.
It's time to forge everything we've covered about the security audit network into a repeatable process that shields your portfolio. This isn't about becoming a security researcher overnight; it's about building a sharp, consistent due diligence habit. The goal is to make security analysis a non-negotiable step in your workflow—forcing you to ask the right questions before connecting your wallet.
Before getting swept up in the hype, anchor your research with a core set of security questions. Think of each one as a checkpoint.
Start with these fundamentals:
Running through these questions systematically strips the emotion out of your decision-making and replaces FOMO with a structured risk assessment.
Use this table to methodically analyze any new protocol. A single "no" isn't always a dealbreaker, but a pattern of red flags should be a clear signal to walk away.
This checklist forces you to slow down and verify claims instead of just taking the team's word for it. It's a simple process, but it's one of the most effective ways to filter out low-effort or dangerous projects.
A project's attitude toward security is revealed by how often it engages with the security audit network. A one-and-done audit is a start, but regular, repeated audits are the hallmark of a mature team. In the broader tech world, latest compliance statistics show that 58% of organizations now conduct four or more audits annually to stay on top of risks. For a trader, seeing a project with a history of multiple audits over time is a powerful signal of its long-term commitment to keeping your funds safe.
Diving into DeFi audits can be confusing, especially when real money is on the line. Let's clear up the most common questions to sharpen your understanding.
No. A solid audit from a top-tier firm significantly reduces risk, but it never eliminates it. An audit is a snapshot in time—it examines the code as it exists during the audit window. It cannot predict bugs introduced in future updates or new types of economic exploits. Treat a strong audit as one critical piece of your research puzzle, not a guarantee of total safety.
First, check the source. A real report should be hosted on the auditing firm's official website or public GitHub—not just the project's blog. Second, research the auditor's reputation within the security audit network. Well-known firms like Trail of Bits, OpenZeppelin, and CertiK have years of public work. An unknown auditor is a major red flag for "auditor shopping," where projects hunt for an easy pass.
The worst thing you can find is a 'Critical' or 'High' severity bug marked as 'Acknowledged' or 'Won't Fix'. This means the team knows about a potentially catastrophic flaw but has decided to launch without fixing it.
An unresolved critical issue is a deal-breaker, plain and simple. It tells you everything you need to know about the team's security culture and their respect for user funds. See this? Walk away.
Generally, yes. Multiple audits from different reputable firms show a serious commitment to security, as each auditor brings a different approach. However, quality matters more than quantity. One comprehensive audit of a project's core logic is far more valuable than three shallow audits of non-critical components. Always check the scope of each report.
Ready to turn on-chain data into your next winning strategy? Wallet Finder.ai gives you the tools to discover, track, and mirror the moves of top-performing DeFi traders in real time. Start your 7-day trial and see what the smart money is doing. Find your edge at https://www.walletfinder.ai.