Guide to Lone Wolf Transactions in DeFi
Discover how lone wolf transactions signal smart money moves. Learn to find and analyze these elite solo traders to sharpen your own DeFi strategy.

February 15, 2026
Wallet Finder

February 15, 2026

A security audit of a website is a comprehensive evaluation of its code, infrastructure, and operational processes designed to uncover and remediate vulnerabilities. In the high-stakes world of Decentralized Finance (DeFi), this is not just a best practice—it is the bedrock of user trust and platform survival. Even a minor flaw can lead to catastrophic financial losses.

In DeFi, your website is the primary gateway for users to interact with high-value assets and sensitive trading data. A security breach here means a direct financial drain and a potential collapse of user confidence. The consequences of skipping a thorough security audit are severe.
Without regular audits, platforms are exposed to risks that can undermine their core value. A compromised API, for instance, could disrupt the instant Telegram alerts that traders on Wallet Finder.ai rely on to mirror smart money moves, erasing a key competitive advantage in an instant.
Imagine a common frontend flaw like a Cross-Site Scripting (XSS) vulnerability allows an attacker to inject malicious code into your platform. Suddenly, user-curated watchlists—containing carefully constructed trading strategies—are exposed. For professional crypto traders and hedge funds, the intellectual property in those watchlists is priceless.
The damage doesn't stop there. A vulnerable endpoint could also lead to the manipulation of displayed data, like profit and loss (PnL) streaks or wallet performance metrics. If users cannot trust the data they use to make trading decisions, the platform's integrity crumbles.
A proactive security audit is the difference between finding a threat in a controlled environment and reading about your platform's exploit on the news. It’s a direct investment in your resilience and reputation.
For DeFi platforms, web interface security is as critical as the smart contracts themselves. The following table highlights common threats that website security audits are designed to find and fix.
These aren't just theoretical risks; they are active threats. A comprehensive website audit is the most important line of defense.
The financial fallout from a breach is staggering, extending beyond lost user funds to include regulatory fines, legal fees, and incident response costs. Reputational damage is often harder to recover from—trust is the ultimate currency in DeFi.
Here are three critical areas where audits provide essential protection:
The threat is escalating. Ransomware attacks, which frequently target web applications and APIs, are projected to jump by 40% by the end of 2026 compared to 2024. This makes routine security audits a non-negotiable part of operations. For more on this, read our guide on conducting a security audit of your network.
A powerful security audit of a website begins with a solid plan. Before testing, you must map out your scope (what to test) and your toolkit (what to use). Without a clear scope, you risk over-testing low-risk areas while critical vulnerabilities go unnoticed.
Think of your website as a city. A smart audit focuses on high-value targets: the banks (payment gateways), the power grid (core APIs), and the city hall (user authentication systems). For a DeFi platform, these critical assets are the lifeblood of your service.
First, map out everything that needs protection. This isn’t just your homepage; it’s every component that handles data, processes transactions, or interacts with users and services. Create an inventory of your most valuable assets to define your attack surface.
Here’s a checklist to get you started:
This mapping exercise creates a clear hierarchy of what matters most. A vulnerability on your "About Us" page is a problem; a flaw in your wallet connection logic is a catastrophe.
Once you know what to audit, you need to decide how. The best approach combines the speed of automated tools with the intuition of manual testing. Using only one method leaves massive blind spots.
The goal isn't just to find vulnerabilities; it's to think like an attacker. Automated tools find the obvious, unlocked doors. Manual testing finds the hidden passages and exploits the assumptions your developers made.
You'll want a mix of Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) tools.
Building a comprehensive toolkit ensures your audit process is repeatable and thorough. For a deeper look, check out our guide on choosing the best security audit software.
With your scope defined and toolkit assembled, it's time for active testing. This phase of the security audit of website blends the speed of automated scanners with the intuition of a human expert. Automated tools cast a wide net, while manual testing is required for complex business logic flaws and unique Web3 attack vectors.
The two methods work together to paint a clear and accurate picture of your security posture.
This foundational flow channels your efforts where they will have the most impact.
Your first line of defense is Static Application Security Testing (SAST). This involves analyzing your website’s source code without running the application. It’s like having a specialized proofreader comb through your code, looking for security mistakes before they can cause damage.
SAST catches issues early in the development lifecycle, making them cheaper and faster to fix. It is particularly effective at spotting:
Integrating a SAST tool into your CI/CD pipeline provides developers with immediate feedback, fostering secure coding habits.
While SAST provides an inside-out view, Dynamic Application Security Testing (DAST) does the opposite. It attacks your application from the outside, mimicking how a real attacker would probe your defenses. DAST tools interact with your live website, sending malicious and unexpected inputs to observe its reactions.
This "black-box" approach is essential for finding runtime vulnerabilities invisible from source code alone, like server misconfigurations or session management flaws.
A DAST scanner doesn’t care if your app is written in Rust, Go, or JavaScript. It only sees the HTTP requests and responses, letting it find vulnerabilities in any web technology, including complex DeFi frontends.
A DAST tool can test for Cross-Site Scripting (XSS), check for insecure server headers, or attempt to access non-public admin pages—issues that only surface when the application is running.
Automated tools cannot understand business logic, context, or the specific risks of Web3 integrations. This is why manual penetration testing is critical for a proper security audit of a website.
A skilled penetration tester thinks like an attacker. They can chain together low-risk vulnerabilities to create a high-impact exploit or find subtle logic flaws that a scanner would miss.
Consider a feature that lets users export their trade history. An automated scanner checks if the button works. A human tester asks the real questions:
These nuanced, context-specific questions require human intelligence. For DeFi projects, manual testing is non-negotiable for verifying wallet connections and ensuring frontend logic cannot be tricked into signing malicious transactions.
Shockingly, 61% of security leaders reported a breach in the last year due to a misconfigured or failed security control. Worse, 65% of those incidents cost over $1 million. You can explore the full cybersecurity statistics on GitProtect.io to see how common these failures are.
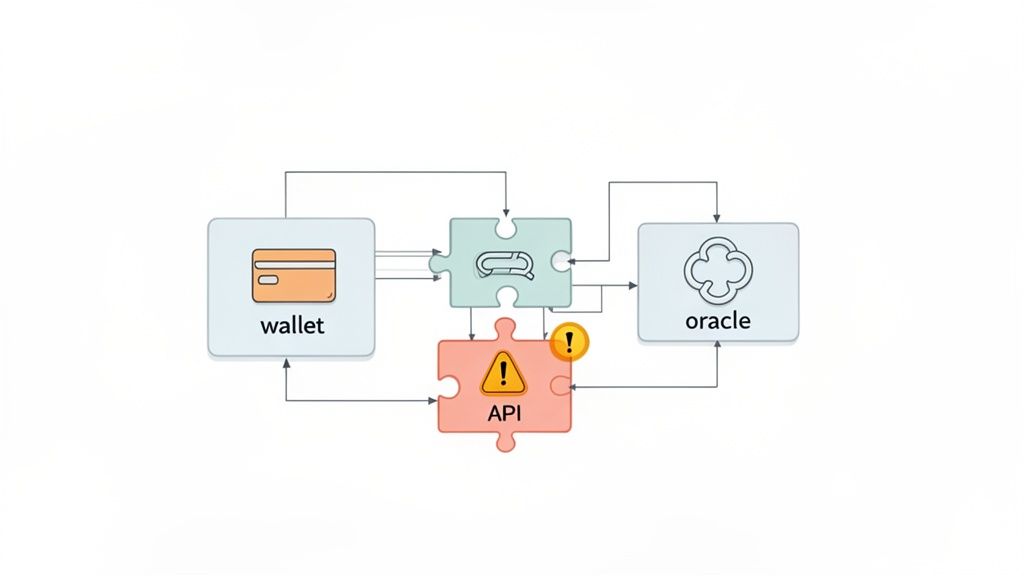
No DeFi platform is an island. Your application is an ecosystem built on third-party libraries, APIs, and blockchain integrations. A proper security audit of a website must go beyond your own code and examine these external components, where some of the biggest risks hide.
When a popular JavaScript library or wallet connector has a flaw, that flaw becomes your problem. This is a supply chain attack—attackers compromise a trusted upstream dependency to gain a backdoor into every application using it.
This threat is growing. In 2024, supply chain attacks impacted 183,000 customers, a 33% increase. Analysts predict that by 2026, 60% of organizations will rigorously vet their partners' cybersecurity risks. You can review the scale of these threats in the latest cybersecurity statistics from SentinelOne.
It’s also why platforms like Wallet Finder.ai ensure their premium services are audited to verify core security promises, like never storing private keys and always using encrypted links.
First, create a complete inventory of every external piece of code your platform depends on. Tools like npm audit or Snyk Open Source automatically scan your dependencies against known vulnerability databases.
But a scan isn't enough. You must also assess the health of each dependency:
A dependency audit isn’t a one-time task. It must be an automated, continuous process integrated into your development pipeline to catch new vulnerabilities as they are discovered.
A DeFi audit must go deeper into the unique components connecting your site to the blockchain. These integrations are prime targets because they directly handle user funds and transaction signing.
Your manual testing should focus on wallet connectors like WalletConnect or MetaMask integrations. Can your frontend logic be manipulated to trick a user into signing a malicious transaction? A common tactic is to alter the transaction details shown to the user while sending something different to the wallet for signing.
Likewise, if you depend on oracles for off-chain data, you must verify their integrity. Examine their security model, resilience to manipulation, and what happens if the oracle provides bad data.
Use this checklist for the Web3-specific parts of your audit. These high-value targets demand extra attention.
This focused approach helps ensure your bridges to the decentralized world are as strong as possible. For a deeper dive, read our guide on smart contract security, as many of the same principles apply.
Finding vulnerabilities during a security audit of a website is just the starting line. A list of issues is useless without a concrete plan to fix them. The real value of an audit comes from transforming raw data into an actionable remediation plan.
Without a clear plan, teams may fix low-impact bugs while a critical flaw that could drain user wallets sits untouched. A structured approach ensures you address the biggest fires first.
Not all vulnerabilities are created equal. A Cross-Site Scripting (XSS) issue on a static "About Us" page is minor. A SQL injection vulnerability in your authentication flow is a "game over" scenario. You need a consistent way to rank these threats.
A risk-based prioritization framework is essential. The industry standard is the Common Vulnerability Scoring System (CVSS), which provides a numerical score from 0 to 10 based on severity. It considers factors like attack complexity, user interaction requirements, and potential impact on confidentiality, integrity, and availability.
Using a framework like CVSS removes guesswork and provides a data-driven way to align everyone—from developers to executives—on what needs to be fixed now.
CVSS provides technical severity, but you must also add business context. A medium-severity vulnerability (e.g., a CVSS score of 6.5) could be catastrophic if it affects a core function like your staking rewards calculator.
To build an effective roadmap, map each finding based on two key metrics:
Plotting these two factors creates a clear prioritization matrix. High-impact, low-effort bugs are quick wins—tackle them first. High-impact, high-effort problems are major projects requiring careful planning.
The goal is to maximize your security return on investment. A smart plan ensures every developer hour spent on fixes delivers the greatest possible risk reduction.
This approach prevents developer burnout from an endless backlog and allows you to demonstrate measurable progress.
Your final audit report is the tool you'll use to drive action. It must be clear, direct, and tailored to its audience. A developer needs technical details, while an executive needs a high-level summary of business risk.
A good report is a blueprint for solutions. Here is a simple structure to align your team:
This structured report ensures everyone is on the same page. It elevates the security audit of a website from a technical check-up to a critical driver of business strength and user trust.
When it comes to a security audit of a website, especially in the high-stakes world of DeFi, a lot of questions pop up. Let's tackle some of the most common ones.
Security is not a one-time task. For any serious DeFi platform, you should conduct a comprehensive, third-party audit at least once a year. However, that is the bare minimum. A continuous vigilance model is essential.
This layered approach maintains a strong day-to-day security posture while preparing for sophisticated, targeted attacks.
Auditing a DeFi website is more complex than a standard web app test. While you still look for classics like XSS and SQL injection, the Web3 layer introduces a new class of high-stakes risks.
Standard web security practices are the foundation, but they aren't enough. A DeFi audit must intensely scrutinize the bridge between your web application and the blockchain, because that's where the money is.
Key areas of focus include:
The best strategy is a hybrid one. Relying solely on a DIY approach or only on external experts creates dangerous blind spots.
You should perform regular, automated security scanning in-house. Using tools like OWASP ZAP or Burp Suite for DAST and integrating SAST tools into your CI/CD pipeline is basic security hygiene. This helps you catch common flaws early and builds a security-first culture.
However, an internal team can develop tunnel vision and may lack specialized knowledge of emerging DeFi threats. For a truly robust assessment, you must engage a third-party security firm that lives and breathes Web3. They bring an attacker’s mindset, sophisticated tools, and hands-on experience that your internal team likely lacks.
Combining continuous internal scanning with an annual expert-led audit creates the multi-layered defense a high-value DeFi platform demands.
Ready to turn on-chain footprints into actionable trading signals? Wallet Finder.ai helps you discover profitable wallets and mirror winning strategies in real time. Start your 7-day trial today and see what the smart money is doing.